Need assistance regarding warning - Class path contains multiple SLF4J bindings
Hi, We have recently migrated our logging framework from log4j1.x to log4j2.17.1 Below are the jars we are using currently in our project. *Please note that we do not have a Mavan/Gradle based project, the dependencies are managed manually.* *Jars : * *log4j-api-2.17.1log4j-appserver-2.17.1log4j-core-2.17.1log4j-slf4j-impl-2.17.1slf4j-api-1.7.31slf4j-log4j12-1.7.31slf4j-simple-1.7.31* *During the project startup we see multiple warning messages as shown below:* SLF4J: Class path contains multiple SLF4J bindings. SLF4J: Found binding in [jar:file:/lib/slf4j-log4j12-1.7.31.jar!/org/slf4j/impl/StaticLoggerBinder.class] SLF4J: Found binding in [jar:file:/lib/slf4j-simple-1.7.31.jar!/org/slf4j/impl/StaticLoggerBinder.class] SLF4J: Found binding in [jar:file:/lib/log4j-slf4j-impl-2.17.1.jar!/org/slf4j/impl/StaticLoggerBinder.class] We are trying to either fix this warning or hide the warning messages from the console but we are unable to do so. Is there any property by which we can hide these or any other way to do the same? Any pointers regarding fixing/hiding the warnings will be helpful. Regards, Nilay
Re: Need assistance regarding warning - Class path contains multiple SLF4J bindings
Hi Nilay, On Thu, 14 Jul 2022 at 09:36, Nilay Prafulla Dhamecha wrote: > SLF4J: Class path contains multiple SLF4J bindings. > SLF4J: Found binding in > [jar:file:/lib/slf4j-log4j12-1.7.31.jar!/org/slf4j/impl/StaticLoggerBinder.class] > SLF4J: Found binding in > [jar:file:/lib/slf4j-simple-1.7.31.jar!/org/slf4j/impl/StaticLoggerBinder.class] > SLF4J: Found binding in > [jar:file:/lib/log4j-slf4j-impl-2.17.1.jar!/org/slf4j/impl/StaticLoggerBinder.class] > > > We are trying to either fix this warning or hide the warning messages from > the console but we are unable to do so. > Is there any property by which we can hide these or any other way to do the > same? The warning is quite explicit regarding the nature of the problem: remove the SLF4J bindings you don't need (probably `slf4j-log4j12` and `slf4j-simple`) and the message will disappear. Piotr
Re: Dependencies for `log4j-jakarta-smtp`
Hi Tim, On Tue, 19 Apr 2022 at 19:32, Tim Perry wrote: > > Will including `com.sun.activation:jakarta.activation` and > `com.sun.mail:smtp` be a problem on application servers > that already include implementations of them? My > knowledge of the J2EE application servers is incomplete > for the modern (Java 11+) versions. You were right on the spot: https://issues.apache.org/jira/browse/LOG4J2-3554 I believe we should remove the implementation artifacts from the POM and leave just the APIs (as `provided`). Piotr
Re: Dependencies for `log4j-jakarta-smtp`
I kind of like Matt's solution of just telling people to exclude those artifacts when they don't need them. Otherwise we'll have the same issue in reverse: requests from people about how to include the "missing" dependencies On Thu, Jul 14, 2022 at 8:56 PM Piotr P. Karwasz wrote: > Hi Tim, > > On Tue, 19 Apr 2022 at 19:32, Tim Perry wrote: > > > > Will including `com.sun.activation:jakarta.activation` and > > `com.sun.mail:smtp` be a problem on application servers > > that already include implementations of them? My > > knowledge of the J2EE application servers is incomplete > > for the modern (Java 11+) versions. > > You were right on the spot: > https://issues.apache.org/jira/browse/LOG4J2-3554 > > I believe we should remove the implementation artifacts from the POM > and leave just the APIs (as `provided`). > > Piotr >
[GitHub] [logging-log4j1] JLLeitschuh opened a new pull request, #21: [SECURITY] Use HTTPS to resolve dependencies in Maven Build
JLLeitschuh opened a new pull request, #21: URL: https://github.com/apache/logging-log4j1/pull/21 [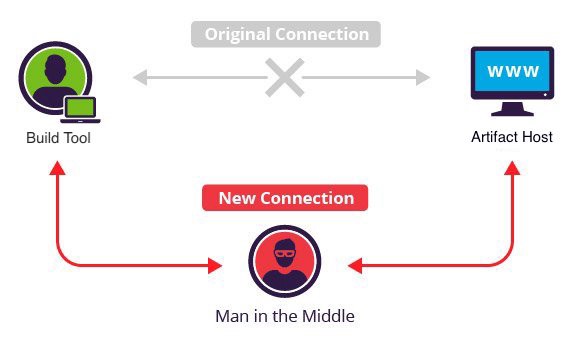](https://medium.com/@jonathan.leitschuh/want-to-take-over-the-java-ecosystem-all-you-need-is-a-mitm-1fc329d898fb?source=friends_link&sk=3c99970c55a899ad9ef41f126efcde0e) --- This is a security fix for a high severity vulnerability in your [Apache Maven](https://maven.apache.org/) `pom.xml` file(s). The build files indicate that this project is resolving dependencies over HTTP instead of HTTPS. This leaves your build vulnerable to allowing a [Man in the Middle](https://en.wikipedia.org/wiki/Man-in-the-middle_attack) (MITM) attackers to execute arbitrary code on your or your computer or CI/CD system. This vulnerability has a CVSS v3.0 Base Score of [8.1/10](https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator?vector=AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H). [POC code](https://max.computer/blog/how-to-take-over-the-computer-of-any-java-or-clojure-or-scala-developer/) has existed since 2014 to maliciously compromise a JAR file in-flight. MITM attacks against HTTP are [increasingly common](https://security.stackexchange.com/a/12050), for example [Comcast is known to have done it to their own users](https://thenextweb.com/insights/2017/12/11/comcast-continues-to-inject-its-own-code-into-websites-you-visit/#). This contribution is a part of a submission to the [GitHub Security Lab](https://securitylab.github.com/) Bug Bounty program. ## Resources - [Want to take over the Java ecosystem? All you need is a MITM!](https://medium.com/@jonathan.leitschuh/want-to-take-over-the-java-ecosystem-all-you-need-is-a-mitm-1fc329d898fb?source=friends_link&sk=3c99970c55a899ad9ef41f126efcde0e) - [Update: Want to take over the Java ecosystem? All you need is a MITM!](https://medium.com/bugbountywriteup/update-want-to-take-over-the-java-ecosystem-all-you-need-is-a-mitm-d069d253fe23?source=friends_link&sk=8c8e52a7d57b98d0b7e541665688b454) - [CVE-2021-26291](https://nvd.nist.gov/vuln/detail/CVE-2021-26291) ## Detecting this and Future Vulnerabilities This vulnerability was automatically detected by GitHub's [LGTM.com](https://lgtm.com) using this [CodeQL Query](https://lgtm.com/rules/155648721/). You can automatically detect future vulnerabilities like this by enabling the free (for open-source) [GitHub Action](https://github.com/github/codeql-action). I'm not an employee of GitHub, I'm simply an open-source security researcher. ## Source This contribution was automatically generated with an [OpenRewrite](https://github.com/openrewrite/rewrite) [refactoring recipe](https://docs.openrewrite.org/), which was lovingly hand crafted to bring this security fix to your repository. The source code that generated this PR can be found here: [UseHttpsForRepositories](https://github.com/openrewrite/rewrite/blob/f8c139d0d66ad9a60ee73b95b7a79571e4820769/rewrite-maven/src/main/java/org/openrewrite/maven/security/UseHttpsForRepositories.java) ## Opting-Out If you'd like to opt-out of future automated security vulnerability fixes like this, please consider adding a file called `.github/GH-ROBOTS.txt` to your repository with the line: ``` User-agent: JLLeitschuh/security-research Disallow: * ``` This bot will respect the [ROBOTS.txt](https://moz.com/learn/seo/robotstxt) format for future contributions. Alternatively, if this project is no longer actively maintained, consider [archiving](https://help.github.com/en/github/creating-cloning-and-archiving-repositories/about-archiving-repositories) the repository. ## CLA Requirements _This section is only relevant if your project requires contributors to sign a Contributor License Agreement (CLA) for external contributions._ It is unlikely that I'll be able to directly sign CLAs. However, all contributed commits are already automatically signed-off. > The meaning of a signoff depends on the project, but it typically certifies that committer has the rights to submit this work under the same license and agrees to a Developer Certificate of Origin > (see [https://developercertificate.org/](https://developercertificate.org/) for more information). > > \- [Git Commit Signoff documentation](https://developercertificate.org/) If signing your organization's CLA is a strict-requirement for merging this contribution, please feel free to close this PR. ## Sponsorship & Support This contribution is sponsored by HUMAN Security Inc. and the new Dan Kaminsky Fellowship, a fellowship created to celebrate Dan's memory and legacy by funding open-source work that makes the world a better (and more secure) place. This PR was generated by [Moderne
[GitHub] [logging-log4j1] garydgregory commented on pull request #21: [SECURITY] Use HTTPS to resolve dependencies in Maven Build
garydgregory commented on PR #21: URL: https://github.com/apache/logging-log4j1/pull/21#issuecomment-1185094237 Closing: version 1.x is EOL. -- This is an automated message from the Apache Git Service. To respond to the message, please log on to GitHub and use the URL above to go to the specific comment. To unsubscribe, e-mail: dev-unsubscr...@logging.apache.org For queries about this service, please contact Infrastructure at: us...@infra.apache.org
[GitHub] [logging-log4j1] garydgregory closed pull request #21: [SECURITY] Use HTTPS to resolve dependencies in Maven Build
garydgregory closed pull request #21: [SECURITY] Use HTTPS to resolve dependencies in Maven Build URL: https://github.com/apache/logging-log4j1/pull/21 -- This is an automated message from the Apache Git Service. To respond to the message, please log on to GitHub and use the URL above to go to the specific comment. To unsubscribe, e-mail: dev-unsubscr...@logging.apache.org For queries about this service, please contact Infrastructure at: us...@infra.apache.org
[GitHub] [logging-log4j1] rgoers commented on pull request #21: [SECURITY] Use HTTPS to resolve dependencies in Maven Build
rgoers commented on PR #21: URL: https://github.com/apache/logging-log4j1/pull/21#issuecomment-1185142283 @JLLeitschuh Please stop creating duplicate PRs -- This is an automated message from the Apache Git Service. To respond to the message, please log on to GitHub and use the URL above to go to the specific comment. To unsubscribe, e-mail: dev-unsubscr...@logging.apache.org For queries about this service, please contact Infrastructure at: us...@infra.apache.org
[GitHub] [logging-log4j1] JLLeitschuh commented on pull request #21: [SECURITY] Use HTTPS to resolve dependencies in Maven Build
JLLeitschuh commented on PR #21: URL: https://github.com/apache/logging-log4j1/pull/21#issuecomment-1185166905 Please forgive me. Do consider archiving the project -- This is an automated message from the Apache Git Service. To respond to the message, please log on to GitHub and use the URL above to go to the specific comment. To unsubscribe, e-mail: dev-unsubscr...@logging.apache.org For queries about this service, please contact Infrastructure at: us...@infra.apache.org
